By Evan Robertson, Sam Bronson, and Daniel Palij
In the lifecycle of a storage medium, it is important to not only consider the purchase and use of a storage medium, but also what will be done with the medium after you have finished using it. SSDs and Hard Drives have an expected life expectancy, after which the risk of degradation of performance increases, which can lead to the unexpected loss of data. When a medium is at the end of its life expectancy, steps should be taken to ensure that the information on the device can be destroyed in such a way that it cannot be recovered.
Decommissioned Storage mediums can act as a weak point in the armor of computer defense. Using software and other tools, information can be extracted from improperly disposed of mediums, including mediums that have been physically disassembled.
Data Sanitation refers to the process of properly deleting the data contained within the storage medium so that it cannot be recovered. Depending on the sensitivity of the data contained within the storage medium, this process may include the proper destruction and disposal of the medium.
The National Institute of Standards and Technology (NIST) Publication 800-88 provides a comprehensive guideline for Media Sanitation at an enterprise level. For individuals, many of the processes are still applicable, and provide a further in-depth analysis on sanitation guidelines.
Hard vs Soft Copy
There are typically two broad data types considered for proper sanitation: Soft and hard copy data. Hard Data refers to the physical research that one may encounter on a day-to-day basis. An example is a printed sheet of paper. These types of Data are more vulnerable to theft if not destroyed properly, as an attacker may simply remove them from the garbage bag or dumpster, giving them unfettered access to the research.
Soft copies refer to the electronic versions of the research that are stored on the storage mediums. These are the things like photos, videos, PDFs, and Word Document. As the Data Security Foundation aims to elevate the digital security standard for researchers, the focus of this article will be on soft copy sanitation.
Classifying Data
First, you must decide how sensitive or important the data on the drive is. This is different for each researcher and must be evaluated on a drive-by-drive basis. For simplicity, NIST uses three levels of sensitivity: Low, Medium, and High. For some research fields, such as healthcare, almost all data will be considered high sensitivity if it includes personal medical information. However, for research that does not have strong compliance rules to navigate, the decision for the classification is up to you. Further into the article we visualize the decision tree that can help determine what steps to take, and this classification helps show where your though process should start.
Broadly speaking, there are three major classifications for the type of data sanitation that can take place with soft copies. The Three Categories: Clear, Purge, and Destroy; each offer different methods and advantages depending on your environment.
Clear
The Clear method is the simplest of three classifications. Through this, users are using the tools built into the drive and the computer to overwrite the data contained in the drive. This can be done through reformatting (i.e. resetting the drive) back to factory settings. Another method is to write over the data, so that the spots on the drive that were previously occupied by the sensitive are replaced with new data that you do not care about. However, advanced forensics techniques can still be applied in this case to recover some of the data from the drive, leaving gaps in the armor.
For more advanced computer users, linux tools such as hdparm can be used to clear the contents of an SSD. In addition to providing tools to securely erase the contents of the SSD, hdparm also provides testing software for the user to ensure that the data that was initially on the drive is no longer present.
This method is most useful when repurposing a drive within the same environment as it was in before, as you can control access. However, if you are planning on selling or disposing of the drive, this method is not enough on its own to ensure that the drive cannot be compromised.
Purge
Purge refers to the methods that render the drive inoperable for any continued use. These methods can also refer to some methods that physically damage the drive itself and share some overlap with the destroy classification depending on the method chosen.
One of the most common methods for purging a hard drive is known as degaussing. Degaussing works by bringing a powerful magnet against the storage plates Because Hard Drives use magnetic fields to hold data, as explained in our article here, the stronger magnet can disrupt and destroy the contents of the drive. Through this, the material on the drive is rendered unreadable and unrecoverable. Furthermore, the hard drive itself is no longer in an operating condition, making this one of the more effective ways of purging a drive.
Degaussing however, does not work on Solid State drives, which do not use magnetic fields to store information, and instead use logic gates to store the data. Because of this, other purging methods should be considered instead to render an SSD inoperable. Unlike Hard drives, which have more mechanical and physical properties that can be exploited to ensure total sanitation, SSDs occupy a smaller footprint and have no moving parts or tools that can be physically manipulated without also destroying the device. If you are an advanced computer user, consider following the advice in the clear section of this article if you plan to reuse the drive for future research work. Otherwise, taking destructive actions to ensure that the data and the drive itself are unrecoverable are the next best steps to ensure data safety.
Destroy
The destroy classification shares many overlaps when discussing sanitation methods regarding soft copies of Data. For example, degaussing fits under the heading of both Purge and Destroy. Because degaussing does not totally destroy the remaining drive, the purge classification remains a better way to categorize it.
The Key difference between purge and destroy is that Destroy not only renders the drive inoperable, but it also ensures that the drive itself is entirely destroyed, with no way to recover any parts of the drive for advanced data extraction. Methods that can be undertaken include shredding the drives, incineration via extreme heat and fire, and drilling through the magnetic plates. Depending on the sensitivity of the data contained within the drive, these actions may be taken alone or alongside the other classifications to ensure complete data security.
The destroy classification is the best option for when a drive is being decommissioned and will not be sold or reused by a researcher or an organization.
Post Sanitation Process
After deciding how to sanitize the storage drive, it is important to not only verify that you have properly sanitized the drive but also document the details of the drive itself. This ensures that you have confidence that whatever happens next with the storage drive the previous data won’t be recovered or stolen.
Verifying that the drive has been properly sanitized can be as simple as plugging the drive in and checking that the old files are not present, to using the hdparm tool to run tests that confirm that the data is overwritten. How in depth the verification process goes is up you; and is all dependent on what you plan to do with the drive in the future.
After Verification, you should document the process as CYA (Cover your Ass) Insurance. If you are working within a group of researchers when a breach of data occurs, you need to be sure that your drives were not the source of the breach. When documenting this procedure, the information you must have will be: Your Name, The Date and Time, The Drive You sanitized, the Serial Number is known, what Methods and Tools you Used, and how sensitive the data was on the drive. In the Event of a breach, having this documentation available will allow you to quickly rule out what drives were not involved, making it easier to find and correct the breach.
How to Decide?
Oftentimes, the decisions as to what steps to take regarding the security of the data is not always clear. There are many factors that will affect the outcome of any data sanitation and how the storage drives will be used in the future. Luckily the NIST 800-88 provides a org level decision chart that can be applied to the individual researcher, making the choice much more clear.
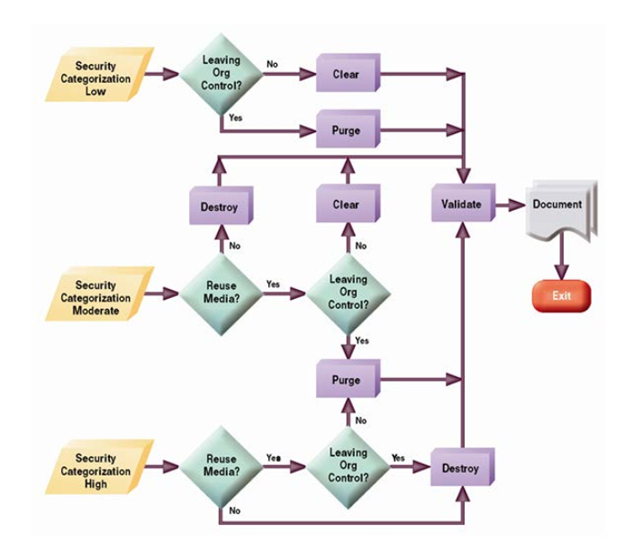
While this article provides the baseline level of knowledge needed to ensure that a storage drive is properly maintained after use, it does not account for the additional compliance needed from certain sectors of research.
If you have found any of this helpful…
Cyber threats don’t wait, neither should you.
- Want to know if your research setup is truly secure?
- Curious to know about potential vulnerabilities in your devices or workflow?
- Looking for actionable next steps tailored to your research needs?
Take our quick self-assessment tool to evaluate your risk level and receive immediate practical recommendations to protect your work.